CorCTF 2022 - “web/jsonquiz” Writeup
Published:
Challenge Description: “How well do you know JSON? Take this quiz and find out!”
jsonquiz
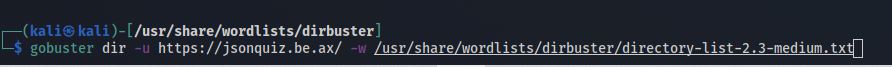
Clicking the challenge link, we are brought to a website. I will first run a gobuster scan using Kali Linux to see if there are any hidden directories we can traverse into.
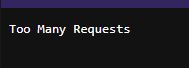
Unfortunately, the website seems to have protections against mass web scanning services by blocking new requests.
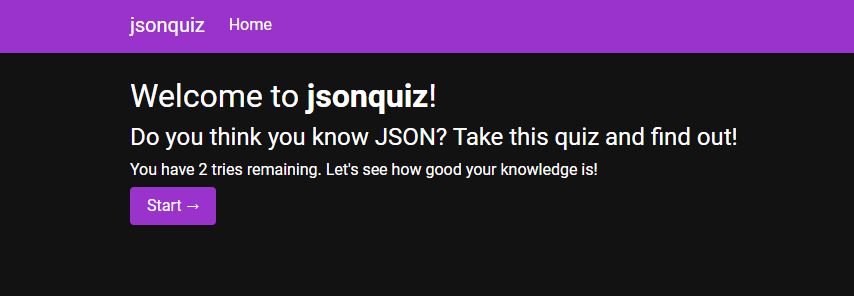
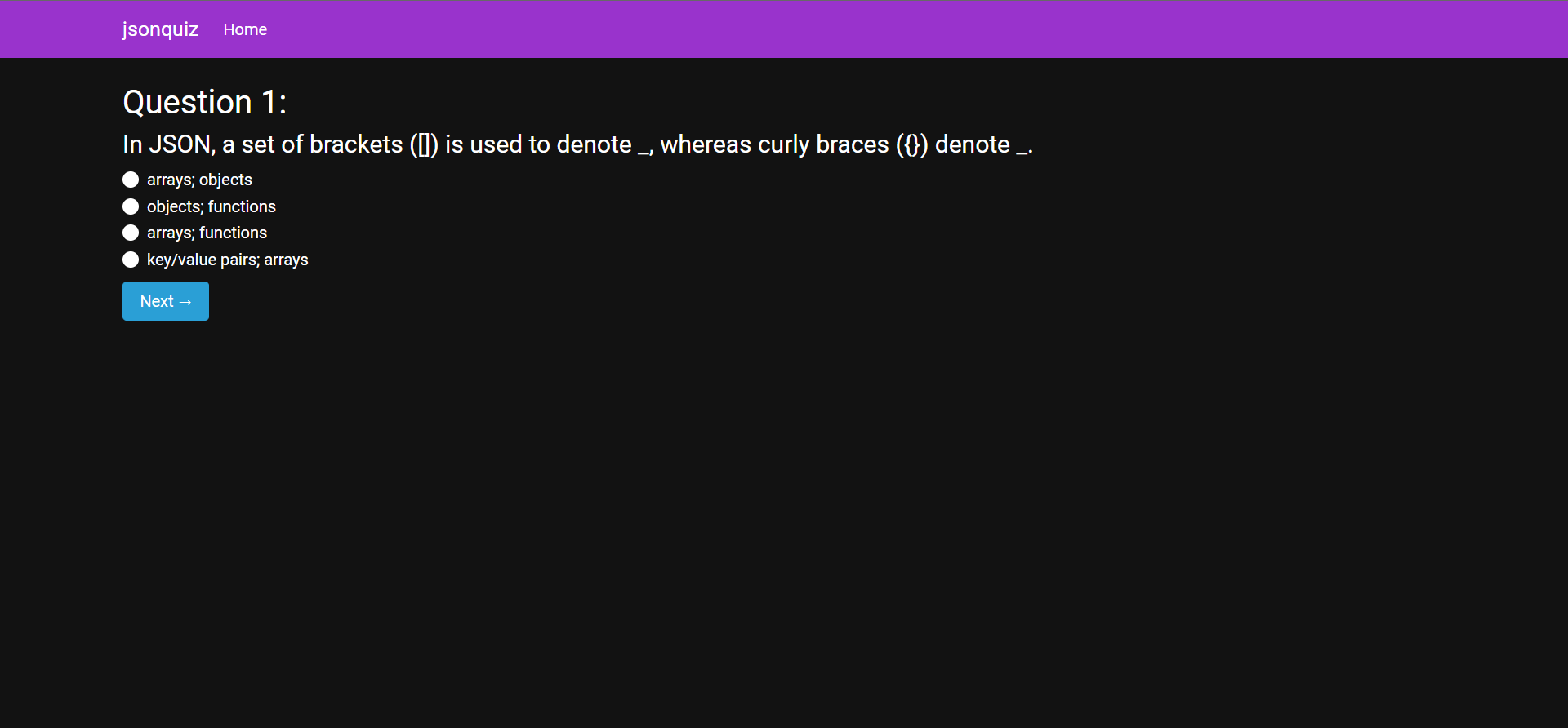
Since there’s only one page to navigate (to my knowledge), we will go ahead and take the quiz to see what’s going on.
After starting the quiz, I’ve noticed a few things. The first is that there are only two tries remaining! The second is that the format seems to be quite similar to the LinkedIn assessment quizzes.
As expected, no matter what I answer, the quiz will always end in failure. It won’t let me retake the quiz, and so we will have to look at the source code in order to see if we can bypass this.
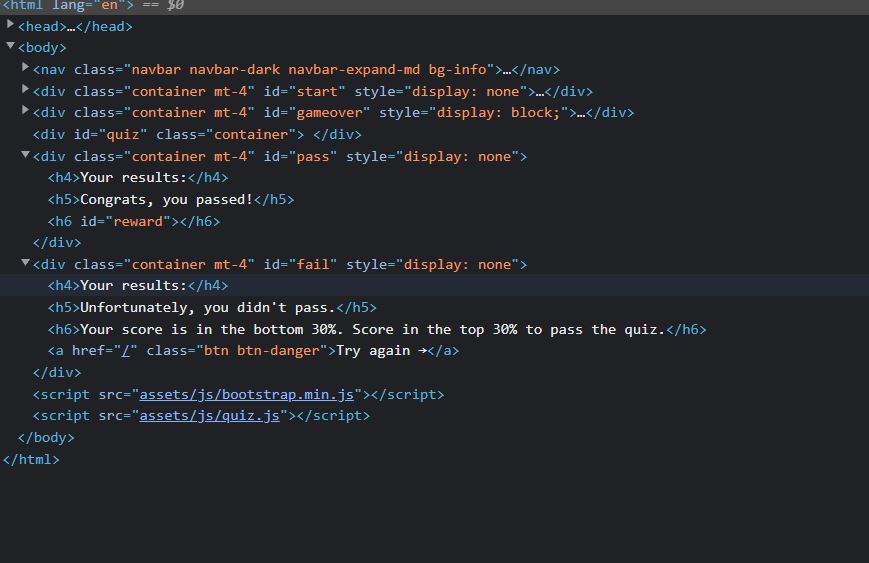
Looking at the HTML, we can see that there is a response (and hopefully a flag) when passing the quiz correctly, so we have to look further into the code to see what can trigger a pass.
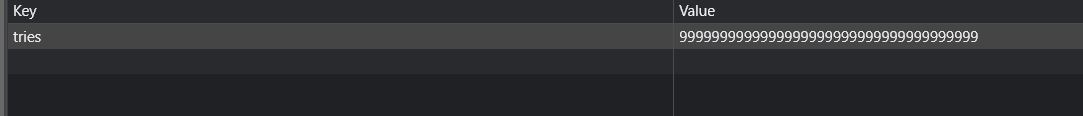
Poking around the cookies and local storage, I found that the website was saving the quiz attempts client side rather than server side, in the local storage. I changed this value to a very large number to see if I could take the quiz again.
This allowed me to take the quiz again, but there’s no point in taking the quiz a billion more times if it leads to a fail every time!
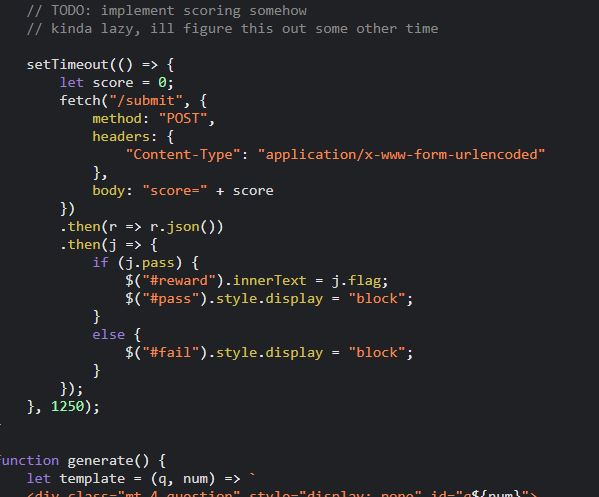
After looking at the JavaScript, I’ve found something that looks promising. It looks like the devs were implementing a scoring feature but were too lazy to actually finish it.
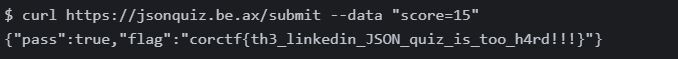
The score is set to a static value, and it seems to get updated via a POST request. The POST request responds with “pass” or “fail” depending on the score, and so we should try sending a request with a passing score. This can be done with Burp Suite or with the code written below.
It returned the flag, corctf{th3_linkedin_JSON_quiz_is_too_h4rd!!!}!